Social Engineering and Taking a Human Error Approach
Written by: Corina Pastore, Engagement Management Lead
When you think of a “hacker,” your mind probably goes immediately to cinematic image of someone with their hood up, with an evil laugh as they type away in a dimly lit room surrounded by screens. Even a Google image search of “hacker” will immediately show this exact image. This depiction, however, couldn’t be further from the truth.
While that method of hacking surely can exist in our world, there are other minatory methods to getting your data that can seize and exploit – with little to no sign of intrusion. One of these methods is coined “social engineering.”
As its name would suggest, “social engineering” is the use of manipulation through human error to procure information and get victims to complete a questionable action. Those actions involve a certain amount of built trust by the Cybercriminal, making social engineering a very emotional method of infiltrating systems.
Phishing – the most popular type of Social Engineering
There are many types of social engineering, and no, none of them have to do with being off the coast of Florida on a boat with chum in the water…
Starting with “Phishing,” where a cybercriminal sends an email pretending to be from a reputable or recognizable company to get personal information and usable data. The term “phishing” in itself is a larger umbrella over different techniques used to phish. These are:
Spam Phishing: An unsolicited email, IM (Instant Message), or social media message that entices you to click and act based on its appearance similarly structured to a well-known, legitimate source. These are often grouped targets, or randomly generated.
Spear Phishing: Also referred to as “whaling,” where a cybercriminal sends above spam to a targeted individual. C-Suite level members are often the target for these types of attacks. The cybercriminal sends an email regarding issues of that are critical to business, appearing as an employee or company with legitimate authority. For example, an attacker may send an email to a CEO requesting payment, pretending to be a client of the company. Or appearing from the company’s tax firm requesting social security numbers of employees from the HR team.
Angler Phishing: This is a newer type of attack that channels social media directly, showing up in users’ inboxes on accounts like Twitter or Facebook, and appears as from a reputable company. These often include links such as the following:
- Paulie Pizza leaves a review on Twitter: “This pizza was cold, and the pepperoni was only on half, and I ordered whole. Won’t be ordering from @PizzaCompany again!”
The above is an opportunity for a cybercriminal to imitate the company @PizzaCompany as a customer service worker account, and say something along the lines of:
- “Dear Customer, we are sorry that we dropped the ball with this pizza! Login to your account at www.pizzacompany.com to access your free pizza to make up for it!”
Seems legit! Right? Especially when clicking through social media, it’s easy to view this as an opportunity for a free pizza and log in.
So how do I protect myself against these types of Phishing attacks?
Starting with the very first and foremost method of protection – verify! Passwords, account credentials, social security numbers–you should always think twice before giving out this information. Always verify who is really on the other end of the line.
Using a Multifactor Authentication method for securing login to systems and applications can limit Spear phishing attack success because even if a password is successfully compromised, without the cybercriminal having your physical device, the password is of no use.
Password Management!!! Building an organizational policy around password management – rotating passwords, requiring password changes every 30-60-90 days, and/or implementing a “required characters” or length of password – are all great ways to add an extra layer of protection. Also, it’s important to not use the same password for everything you access.
Companies can build training programs to raise awareness of the various threats in the workplace through email, direct messages, and learn the signs of a phishing scam. Here are some top items to look for:
- You can always hover your mouse cursor over any link in an email, and it will show the REAL URL you would be taken to. If the URLs match, it is likely safe to access. If the URLs do not match, it is suggested to report this email as spam, delete, and follow your organizational procedures to escalating phishing and spam attempts.
- Note the items as part of the email. Check the entire sender email address, look for requests for personal information, verify the sender signature, and look for any odd email addresses in the CC of the email.
- Content can play a huge role as well in these types of emails, and you should also look for any sort of attachments that require installation, enabling macros, or adjusting any sort of settings.
- Are there misspellings or grammatical errors? Odd formatting? It’s likely that something that is legitimate will not contain these types of things.

Implementing protection such as Microsoft Defender for O365 to help protect email, files, and online storage is also a great way to ensure organizational security. It can help prevent a wide variety of volume-based and targeted attacks, including business email compromise, credential phishing, ransomware, and advanced malware with a robust filtering stack.
All Lines Technology has the resources in place to help your organization learn these threats, understand your organizational security posture, and put together an assessment of your environment to align your company with the best practices. Check out our Cybersecurity Program offerings – Managed services, and consulting!
Now that I understand Phishing and what to look for, what else should I know?
Unfortunately, there’s quite a few other ways that Cybercriminals can work to access your data through non-phishing methods of social engineering. These are:
- Smishing – The use of text message to trick an individual into clicking a link or downloading malicious content via smartphone.
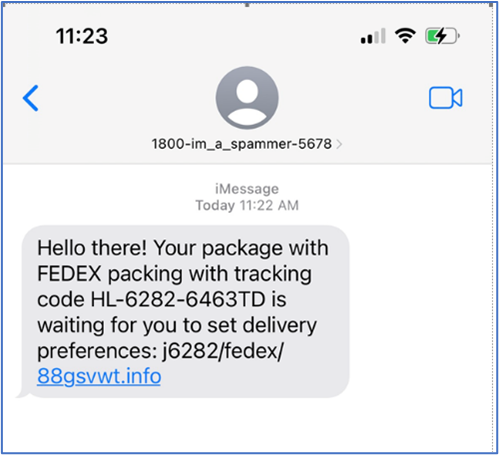
The link typically points to a site hosting malware or prompts the user to log in to their account. The authentication page is not on the official FedEx site, but it’s more difficult to see the full URL on a smartphone browser, and many users won’t bother checking.
- Vishing – a social engineering trick that a cybercriminal will utilize a scare tactic text message with a phone number to “call for immediate action” or “call to learn more.” The attacker convinces the individual to charge their credit card or transfer money directly into the criminal’s account posing as a member of a trusted company or government branch. You can see this commonly with cybercriminals posing as IRS agents demanding payments.
- Baiting – This is a bit more direct and can be easier to spot in the professional world. Cybercriminals, with bating, use a luring tactic to trick individuals into clicking links or downloading malware. Examples of this:
- “Congratulations! You are the lucky winner of a brand-new Tesla! Click this link to claim it.”
- A Cybercriminal goes to a local coffee chain and leaves a USB drive filled with malicious content, and someone unsuspecting picks it up curious what’s on it and plugs it into their device.
- Physical Breaches – This is very direct, and it is important to identify if there is an individual attempting to gain access to a secure area. A way attackers do this is by seeming social and familiar, and using your politeness against you, such as you hold the door for this person if they follow closely behind you. Or they can gain access to an office by pretending to be on a phone call while breezing past security or a front desk.
- Quid Pro Quo – A quid pro quo attack is also known as a “something-for-something attack.” It is a form of baiting, as attackers offer victims a service or benefit if the latter perform specific tasks or give out information or access.
- Scareware – The intent of scareware is to frighten the computer user into paying for fake software or to further infect a computer system. To frighten users, scareware presents the user with a variety of pop-up security alerts that appear as warnings from actual antivirus companies, frequently claiming that the user’s files have been infected. If the tactic works, the victim downloads fake software that is malicious in nature and risks the individual’s personal data.
How can All Lines Technology Help?
All Lines Cybersecurity team has many options of support for your organization – from awareness and training to assessments and reviews of your company’s security posture. Check out our offerings here, and see if we’d be a great fit for you to help empower you to protect your environment!
